Table of Contents
Recently, some readers reported that they encountered a registry key for debuggers.
Updated
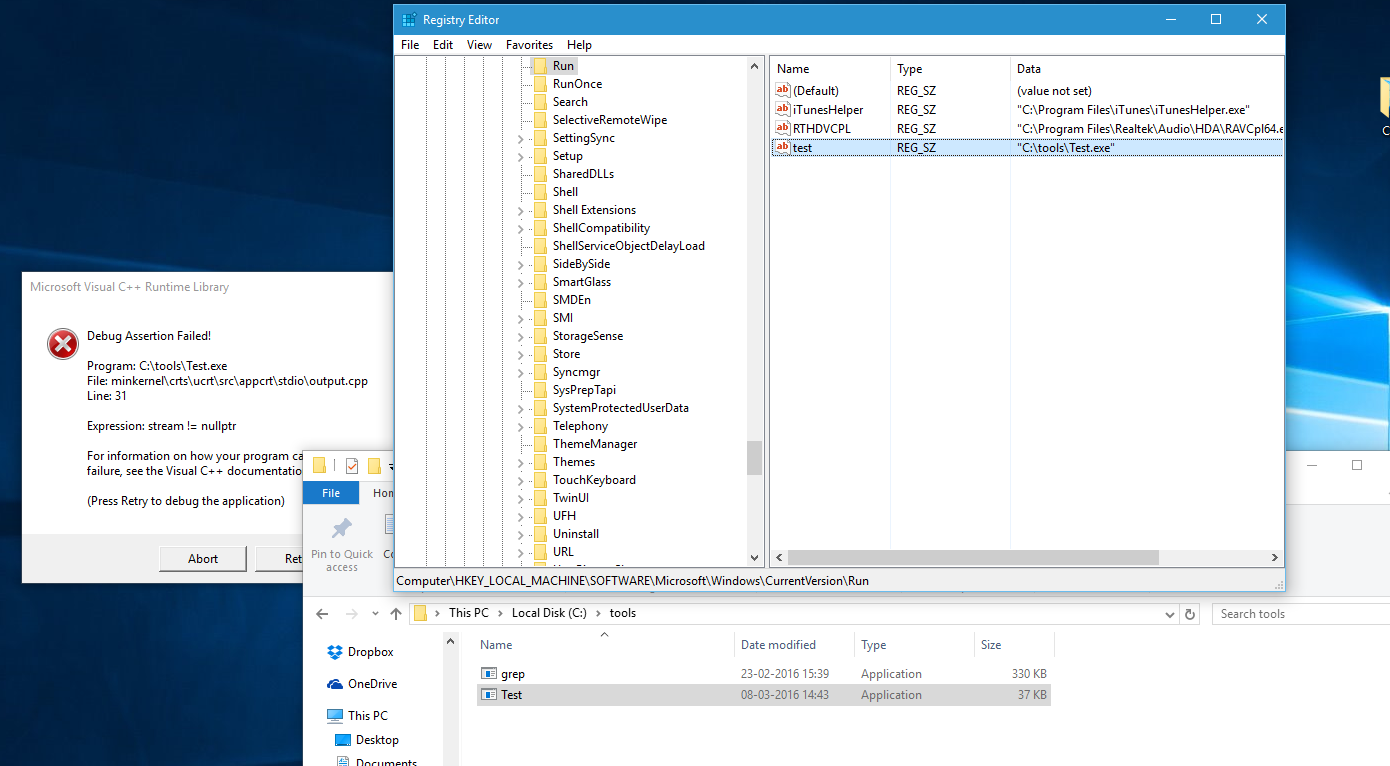
To assign a debugger other than Postmortem Debugger, navigate to the following registry key: HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows NT CurrentVersion AeDebug Add or change the debugger value using the REG_SZ line, which clearly represents the command line that the debugger should specify.
Updated
Are you tired of your computer running slow? Annoyed by frustrating error messages? ASR Pro is the solution for you! Our recommended tool will quickly diagnose and repair Windows issues while dramatically increasing system performance. So don't wait any longer, download ASR Pro today!

Describes these guidelines, location, policy values, management, and then security considerations for debugging program security policy settings.
Link
This policy setting determines which players can attach public actions or any actions, even processes that they specifically own. Developers debugging their own functions do not need this user right. This user right is required by developers who are debugging new system components. These user rights promise access to sensitive and important components of the operating system.
Possible Values
Best Practices
Location
Default
The table contains actual and effective policy numbers by defaultThe default for the latest supported versions, most commonly associated with Windows. The default values are also listed at the top of the policy properties page.
| Server type in addition to GPO | Default |
|---|---|
| Default domain rule | Not defined |
| Default domain controller policy | Administrators |
| Standalone Server Defaults | Administrators |
| Ultra-trusted default domain controller settings | Administrators |
| Actual default member server settings | Administrators |
| Actual default settings for client computers | Administrators |
Rules Management
This section describes the features and then the tools to help someone manage this policy.
A restart of the device is not required for this policy setting to take effect.
Any changes to the assignment of custom rights to an account may take effect the following time:The current login of the account owner.
Group Policy
Settings are applied in the following order by a Group Policy Object (GPO) that overrides our own settings on the local computer the next time Group Policy is refreshed:
- Local policy settings
- Site policy settings
- Domain insurance protection settings
- Unit policy settings
If a local setting is simply not available, it means that the setting is currently controlled by a GPO.
Security Issues
How to attach a debugger to a process or kernel?
Accounts with certain “Debug Programs” user rights can attach an actual debugger to any process or to that kernel, giving full access to sensitive and therefore critical components of the operating system. This right can be granted to standard learning administrators. Check the current setting in the Local Group Policy Editor. Run gpedit.msc.
This section explains how an attacker can use the exploit you are running or its configuration, how this particular countermeasure is implemented, and the potential negative consequences of implementing a countermeasure.
Vulnerability
The debug user right can be used to retrieve sensitive device specifications from system memory, or to access and modify kernel or application structures. Some tools Ravage uses this user rights fragment, which can hash passwords and other private security measures or inject malware.By default, the Debug this program user right is restricted to administrators, which reduces the risk of this type of vulnerability.
Countermeasures
How to enable debug logging in the REGEDT32 registry?
To enable debug logging, set the new debug flag on the PC and restart the service by doing most of the following: Start the Regedt32 program. Delete the Reg_SZ value from the following PC registry entry, create a REG_DWORD value with the same name, then add the hexadecimal value2080FFFF.
Remove accounts from all communities that do not require program debug user rights.
Potential You Can Influence
If a user’s right is revoked, no one can debug systems. However, typical circumstances rarely require this volume on production equipment. If you encounter an issue that requires you to debug your application on a production server, you can reassign the server to a different organizational product (OU).temporarily and assign male or female debugging rights to a separate group policy corresponding to this division.
I’m trying to find PC keys that Were modified by the “Debug programs” security policy (also known as SeDebugPrivilege) using 8 windows.
I remember once seeing a site that defined every important PC registry based on a policy setting, but I couldn’t find it.

All my research on SeDebugPrivilege, the registry key, doesn’t seem to provide any further information.
Does anyone know how many keys this Pengaturan changes and/or how to find out?
Policy Path:
Computer ConfigurationWindows SettingsLocal PoliciesUser Rights Assignments
Default:
Supported:
at least Windows XP SP2, Windows Server 2003
Registry Settings:
User rights security settings are not computer registry keys
Reload Required:
Is it possible to whitelist a registry key as a debugger?
From what you say, it would be a shame if our own executable that acts as a debugger was very heavily whitelisted, such a registry key is indeed flagged as malware and the only way to prevent this is to simply add a key registry whitelisted. The problem with this approach is that the names of the registry keys cannot be predicted in advance.
This user has the best control over which users can attach the latest version of the debugger to any process or this kernel. Developers debugging their work do not need to be assigned user type rights. Developers from For newbie system components, it is necessary that this user be able to do this. This user right provides full access to very important and important components of the operating system.
What is the debug programs user right for?
Debugger user accounts can add the debugger to any process or, if desired, to the kernel, ensuring a full load with sensitive and critical components of a production application. In the standard configuration, this right is assigned to administrators.
Assigning this user right can be a security risk. Assign this user right only to the users you want.
Install SQL Server 2008 – Access Denied
The RDBMS installer is an administrator and therefore can have full privileges.
2012-03-22 14:29:25 SQLEngine: waiting for --sqlserverservicescm: for nt event 'GlobalsqlserverRecComplete$DBMON' to createMar 22, 2012 2:29:30 PM SQLEngine: pending --sqlserverservicescm: on NT event "GlobalsqlserverRecComplete$DBMON" or SQL process handle to reportMar 22, 2012 2:29:30 PM Slp: Failed to configure action for SQL_Engine_Core_Inst functions during ConfigRC sync and according to ConfigRC script.2012-03-22 14:29:30 slp-access: considered denied
What is the purpose of the debug programs user right?
By default, the Debug Programs user right is granted only to administrators, which helps mitigate all of these vulnerabilities. Remove accounts from all viewers and groups that do not require the “Debug someone’s programs” user right. If buyers revoke this user right, no one will debug programs.
2012-03-22 14:29:31 Slp: Sco: Trying to copy hklm SOFTWAREMicrosoftMicrosoft SQL Server registry key to document C:Program FilesMicrosoft SQL Server100Setup BootstrapLog20120322_142338 for distribution Registry_SOFTWARE_Microsoft_Microsoft SQL Server.reg_2012-03-22 14:29:31 Slp: Sco: P trying to delete hklm SOFTWAREMicrosoftWindowsCurrentVersionUninstall registry key in C:Program FilesMicrosoft SQL Server100Setup BootstrapLog Write20120322_142338 in Registry_SOFTWARE_Microsoft_Windows_CurrentVersion_Uninstall.reg_2012-03-22 14:29:31 Slp: Attempt to write sco: hklm SOFTWAREMicrosoftMSSQLServer registry key time for file C:Program FilesMicrosoft SQL Server100Setup BootstrapLog 20120322_142338Registry_SOFTWARE_Microsoft_MSSQLServer.reg_2012-03-22 14:29:31 Slp: Sco: Trying to hklm in your computer's Windows registry SOFTWAREWow6432NodeMicrosoftMicrosoft SQL Server key to file C:ProgramsMicrosoft SQL Server100Setup Bootstrap WriteLog 20120322_142338Registry_SOFTWARE_Wow6432Node_Microsoft_Microsoft SQL Server.reg_2012-03-22 14:29:31 Slp: Sco: Attempt to write hklm SOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionUninstall key to PC in C:Program FilesMicrosoft SQL Server100Write Setup Bootstrap Log 20120322_142338Registry_SOFTWARE_Wow6432Node_Microsoft_Windows_CurrentVersion_Uninstall.reg_2012-03-22 14:29:31 Sco:slp: Attempted to write registry key hklm SOFTWAREWow6432NodeMicrosoftMSSQLServer to history C:Program FilesMicrosoft SQL Server100Setup Bootstrap Log20120322_142338Write Registry_SOFTWARE_Wow6432Node_Microsoft. reg_03/22/2012 02:29:32 PM SLP: access denied
The above errors are required to run the installer. What you have done is half of the installation. The RDBMS is installed but built as a single user. Some permissions may be missing, the sa password is empty. AccountingService APIs are not getting the permissions these people need. The agent does not start for these reasons.
Attempt 1: Remove User Account Control restrictions available to users installing SQL Server. Restart and try again. No luck.
Attempt 2: Add service sites to the Administrators group. I don’t know why I was looking for this other than desperation to get it to work. Service accounts usually get their permissions during installation because they are included in convenient SQL Server permission groups. Restart the server to try again. Bad luck
Speed up your computer today with this simple download.