Table of Contents
If you have three types of spyware installed on your computer, this guide will help you fix them.
Updated
g.There can be several types of spyware, for example, hacker technologies, adware, keyboard recorders, and many others. Each type of malware has its own unique way of working.
g.
Technically, I contracted email errorsFeeds and images simply from patrimonio Designs on Fotolia.com

Spyware is a program that can access a computer without the user’s consent. Some spyware is associated with security and data issues that can disrupt the functionality of your laptop, desktop, or network, while others only collect information about your web browsing habits. As a workaround, it’s worth keeping up with the latest spyware threats and then being able to detect any signs that your current system is infected.
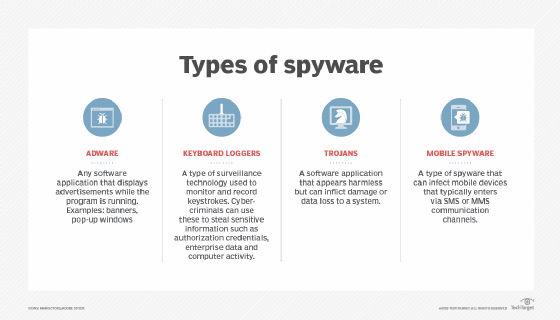
Adware
Adware is a typical spyware that is primarily used on cellular networks. When you log in, it records your amazing browsing habits to gather information on the types of websites you are looking for. Information used to target pop-up marketing messages and spam.
Keyboard Recorder
Keyboard spyware is malware used by hackers. This program is designed to obtain personal informationInformation that will record the actual keystrokes you enter on your computer. If you enter your PIN, password, or credit card number yourself, the Keyword Recorder will save them to work with the hacker. This information can be used to gain access to systems and commit identity theft and fraud.
Modem Hacker
Updated
Are you tired of your computer running slow? Annoyed by frustrating error messages? ASR Pro is the solution for you! Our recommended tool will quickly diagnose and repair Windows issues while dramatically increasing system performance. So don't wait any longer, download ASR Pro today!

Connect a modem to your phone line to host unauthorized webinars and access participants’ websites over an Internet connection. Typically, this spyware is a program designed to call premium phone numbers in addition to accessing websites such as adult sites. You don’t know anything about access and call until you see an unauthorized rate in your bill.
Browser Hijackers
Browser hijacker affects your internet access when you reset your home page and bookmarks. Of course, the goal is to use commercial spam to guide you to unwanted sites.These programs are always minors who record your online activity and advertise and sell information to advertisers.
Commercial Spyware
What are the 4 types of spyware?
Spyware is mainly divided into four types: adware, system tracking, tracking including web tracking, and Trojans. … … Examples of other notorious types include online digital rights management, home phone features, keyloggers, rootkits, and web beacons.
What are the main types of spyware?
Adware. Adware is a very common type of spyware that is primarily used by advertisers.Keyboard recorder. Keyboard Logger Spyware is malware used by hackers.Modem hacker.Browser hijacker.Commercial spyware.
Almost all spyware is not unauthorized. In some cases, companies offering free software and social media need platforms to hide you with spyware in order to gain access to systems. They will then receive a direct mail for you while using their system. In this case, access to free software is part of your privacy.
Scott Yoder is a professional writer and editor specializing in creating online marketing materials. He graduated from Oregon State University with a BA in English. Originally a teacher and resume writer in public education, he now writes extensively on internet marketing, environmental business, technology, law and more.wasps, medical topics.
B
In this article, we share what spyware is, common methods spyware uses, and how you can use spyware to protect yourself, your employees, and your data.
What Is Spyware?
Spyware is a malware factor that constantly monitors Internet activity and usage of your wonderful computer. Its purpose can be to collect information, often mainly related to traffic data, including keystrokes, screenshots, web pages visited, or various types of sensitive or confidential information. However, the data can be used in many ways, including selling to interested businesses, or perhaps in some cases, identity theft. It is very important to understand these common types of spyware and what they can detect.
What is spyware and its types?
Spyware related types Spyware is not only a software type. This is a whole category of malware, which includes adware, keyboard recorders, Trojans, and programs to steal information from mobile devices.
An installation can be infected with spyware in the same way as other types of malware, including Trojans, computers, worms, etc. They can support various security vulnerabilities such asWhere the user clicks on the email. unknown website or simply by visiting a suitable malicious website. Users can download anything that is advertised as “All Useful Tools” or as a free application (free software).
Why Is Spyware So Important?
When performing daily phishing attempts, it is very important that your employees are well trained in how individuals can prevent and detect phishing attacks. We’ve seen how email threat prevention companies have always been fooled by various phishing attempts as they have become more difficult to detect these days. Many people imagine themselves as guys in disguise that you know and with whom you regularly correspond. More recently, the CEO of the company was scammed and tried to sell hundreds of thousands of dollars to recover his data. People are the first and last line of defense, so what can be avoided is also important for school staff.
How To Determine If Your Computer Is Infected With Spyware
You canYou are better off recognizing this type of software if you have up-to-date firewall, anti-virus or anti-virus software installed on your device. They will be on the lookout for suspicious activity or other security threats on your PC.
Other notable flaws may indicate that one or more spyware parties have been integrated into the system. They rarely only work on your computer system, which means that your device can suffer from some infections. In this scenario, users will notice a specific decrease in system performance over time, such as high CPU usage, disk usage, or unexplained network traffic.
When using various offers and applications, this can regularly lead to freezes, startup errors, or even problems connecting to the World Wide Web. Certain types of spyware can also remove your firewall and other web browser security settings in addition to your antivirus, increasing your risk of future infections. EIf customers experience any of these issues, it is possible that spyware or other types of malware have infected your system. Yes
What Are The Most Common Types Of Spyware?
In general, the functionality of a particular malware depends on the intentions of its author. Here are four examples of the most common types of spyware.
Keyloggers – Also known as keylogger system monitors, they are developed in the market to record your computer’s activity including keystrokes, learning history, electronic activity. -mail, chatting, site access, system credentials, etc. More The complex examples above can also collect documents intended for printers. Thieves
Password. As the name suggests, all types of spyware hijack all accounts inserted into the infected device. They probably contain similar system credentials as well as other very important passwords.
Infostealer. If a computer is infected with spyware in addition to another device, it may expose the confidentity information such as passwords, usernames, email addresses, log files, browsing history, network information, spreadsheets, documents, media files, etc. Information thieves typically exploit browser security holes to collect personal information and other important information.
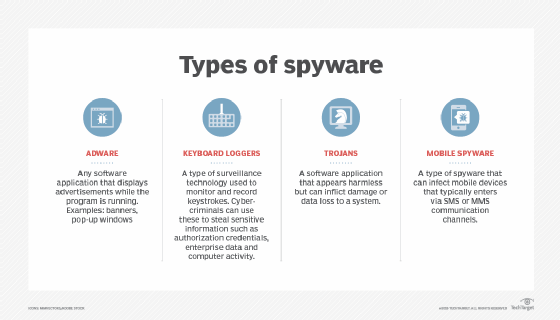
Banking Trojans. Like information theft, banking Trojans exploit security holes in browsers to obtain access data using financial institutions, altering the content of transactions or websites, or inserting additional transactions, including online portals, brokers, digital wallets and in addition, victims of these banking Trojans often become all kinds of other financial institutions.
Conclusion
There are risks inherent in digital home theater systems, just like spyware or other types of malware. Fortunately, there are several people and tools that can help you, and your business will be protected from these online threats as well.
Speed up your computer today with this simple download.ИСПРАВЛЕНИЕ: три типа шпионского ПО
CORREÇÃO: Três Tipos De Spyware
FIX: 3가지 유형의 스파이웨어
FIX: Drie Soorten Spyware
POPRAWKA: Trzy Rodzaje Oprogramowania Szpiegującego
FIX: Drei Arten Von Spyware
FIX: Tre Typer Av Spionprogram
FIX: Tre Tipi Di Spyware