Table of Contents
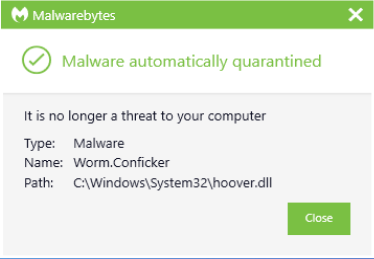
Sometimes your system may display a message that Malwarebytes is removing Conficker. There can be several reasons for this error.
Updated
g.Malwarebytes can detect worms and remove them accordingly. Conficker without another user’s interaction with your dog. Download Malwarebytes to your desktop. Once Malwarebytes for Windows is installed, the program will open the Malwarebytes welcome screen.
Malwarebytes detects and removes the worm very efficiently. Conficker without further user interaction. Download Malwarebytes to your desktop. Once Malwarebytes for Windows is installed, the program will open the Malwarebytes welcome screen.
g.TO
Understand that Malwarebytes Anti-Malware still won’t be able to handle it with this little devil.
I’ve been using Malwarebytes Anti-Malware for about a year now, and I scan regularly.
I have not been able to access any of these websites in the past month:
After troubleshooting network or modem problems, I came to the conclusion that this is some kind of malware and it is rather difficult to find a solution if you do not have access to the pages of the refuge.
Half an hour ago after using the Conficker firewall removal tool, everything is back to normal, I can access all of these sites, but update normally.
The information in this knowledge base is intended for corporate environments in which system administrators can implement the details described in this article. There is a reason not to use this article if this antivirus cleans up the virus properly and your systems are completely restructured. To make sure your system is virus-free, immediately scan from the following website: http://www.microsoft.com/security/scanner/
Does Malwarebytes protect against worms?
Malwarebytes can detect worms and remove them without further user intervention.
You can find detailed information about the Conficker virus at the following Microsoft website:
Therefore, be careful It is important to clean the media so that the threat does not spread to already cleaned systems.
Note. The Win32 / Conficker.D variant does not spread over an absolute network to removable drives or shared folders. Win32 / Conficker.D is installed by previous versions of Win32 / Conficker.
This procedure does not remove certain Conficker malware from the system. This function only stops the spread of spyware and. You must use an antivirus that can remove Conficker malware from the plan. Or follow the steps in “ Manual steps to remove Win32 / Conficker, the most important virus >” See this knowledgebase website for manual removal of malware from the system.
Based on the needs of your environment, create a new Group Policy (GPO) concept that will apply to all computers in a specific organizational unit (OU), location, or region.
HKEY_LOCAL_MACHINE Software Microsoft Windows NT CurrentVersion Svchost
This will prevent the actual creation of a malicious service from accidentallyname in the netsvcs registry value.
Set this policy to return write and delete permissions for the% windir% Tasks folder. This prevents the Conficker malware from creating scheduled tasks that could re-infect the system.
Disable autorun (autorun) functions. Prevents the spread of Conficker malware by using built-in Windows autorun functionality.
Note. Depending on the version of Windows you are actually using, different updates must be installed to properly disable the Autoplay feature:
Remove systems and malware after distributing Group Policy settings.
Microsoft Protection Center malware must have an updated Microsoft security scanner. It is definitely a standalone binary that is useful for removing common malware and / or can help remove the Win32 / Conficker adware and spyware family.
Does Malwarebytes protect against worms?
Malwarebytes can detect and remove worms without further interaction with the end user.
Note. Microsoft’s security scanner does not necessarily prevent new infections because it is not considered an antivirus program.working in real time.
You can download the Microsoft Security Scanner directly from the Microsoft Do-Site website:
Updated
Are you tired of your computer running slow? Annoyed by frustrating error messages? ASR Pro is the solution for you! Our recommended tool will quickly diagnose and repair Windows issues while dramatically increasing system performance. So don't wait any longer, download ASR Pro today!

Whenever possible, it is important that you do not log on with a domain account. Do not actually log in with a domain administrator account. The malware impersonates logged in user access and network resources and uses logged in user credentials. This behavior allows malware to spread.
Stop the server service. Remove this provided by your system administrator to prevent malware from spreading with this essential method.
Note. The server service should not stop temporarily while you clean up adware and spyware in your environment. This is especially true for production servers as this step is expected to affect the availability of network resources. Once the environment has been largely cleaned up, the server service can be reactivated.
To stop the server service, use the conMicrosoft Management Salts (MMC). To do this, do one of the following:
Follow these steps to stop the Task Scheduler service in Windows Vista or Windows Server 2008. Topic
It is important to note that this method or step contains steps that will tell you how to change the registry on the market. However, serious problems arise if you incorrectly edit the registry. Therefore, be sure to follow these steps carefully. For added protection, you need to rebuild the registry before modifying it. Then you can restore the registry if you run into problems. For more information on tips for backing up and restoring the Windows registry, click the following article number to view a specific article in the Microsoft Knowledge Base:
Note. The Task Scheduler service should be temporarily disabled only while your environment is cleared of malware. This is especially true in real-world Windows Vista, as well as Windows Server 2008, as this step destroys various built-in scheduled tasks. Once the environment is clear, repeatbut activate the server service.
If the infected computer is infected with the Win32 / Conficker virus, a random service detection will be added to the list.
Note. In Win32 / Conficker.B, the list service consisted of random letters and could be at the end of the list. In the following variations, the naming service can appear anywhere in the list and appears to be more legitimate. If the random phrase service is not listed below, check your system against the “Service Table” in this procedure to see which naming specialist may have been added by Win32 / Conficker. To check, compare the list in the “Service Table” with a similar system that is not considered infected.
Note the full name of the malicious service. You will actually need this information later in this procedure.
We delete our line indicating the type of malicious service. Be sure to leave a new line blank under the last valid entry in the list and click OK if necessary.
Inherit from old authorization records that apply to a single object. Add them to the entries explicitly listed here.
Replace the authorization entries for all child objects with the entries shown here that apply to child device objects. You
What does the Conficker virus do?
Once Conficker infects a computer, it disables many security features and automatic assistance settings, deletes restore points, and opens contacts for instructions from a personalized remote control. After configuring the first computer, Conficker uses it to access the rest of the network.
If you are using Windows 2000, Windows XP, or Windows Server 2003, install the updated version 967715.
For more information, click the following version number to view the Microsoft Knowledge Base article:
Is Conficker still active?
Compared to nine years after infecting millions of systems worldwide, the malware remains very active, according to a Trend Micro report. Nonetheless, Confiker’s detection has consistently stood at over 20,000 per month over the past few years, which suggests that he is undoubtedly still very active.
Enter this on the command line using the following commands. Press ENTER after each command:
After each order request, you will receive a message that usually looks like this:
SERVICE_NAME: wuauserv
TYPE: 20 WIN32_SHARE_PROCESS
STATUS: 4 WORKING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE: 0 (0x0)
SERVICE_EXIT_CODE. 1 (0x0)
> BREAKPOINT: 0x0
WAIT_HINT: 0x0
In this case, “STATUS: 4 RUNNING” indicates that part of the service is running.
To check the history of the SvcHost registry subkey, follow these steps:
Antivirus package vendor list 49500
If you do not have an antivirus vendor or if you have an antivirus vendorIf this software cannot help you, please contact Microsoft Consumer Services for assistance.
Restore the default permissions for the SVCHOST registry key and task folder. You should restore the legacy settings by using the Group Policy settings. If only one policy is removed, the permissions to go to default settings should not be changed. For more information, see the Table of Standard Resolutions in Each Category “ Mitigation Actions “.
If you have any doubts about identifying systems infected with Conficker, the details on the TechNet blog below may help:
Is Conficker still active?
When it first appeared worldwide in 2008, Conficker infected 9 million systems worldwide to the world, making it one of the most prolific Trojan horses of the year. However, Conficker detection has been steady at around 20,000 per month over the past few years, suggesting that this task is still very active.
What does the Conficker virus do?
Once Conficker infects a computer, it disables many security features and automatic backup settings, deletes restore points, opens connections for instructions from a remote computer. After the computer itself is configured, Conficker uses the problem to access network relaxation.
What is a Conficker attack?
Conficker is a netbook worm developed by malware authors to infect Windows computers with vulnerabilities (MS08-067) and spread the infection to help other Windows computers that are so vulnerable that they simply connect to the network without human intervention. It is also called daunadup.
Действия по восстановлению удаляют Malwarebytes Conficker.
Los Pasos De Recuperación Eliminan Malwarebytes Conficker.
Kroki Odzyskiwania Usuwają Malwarebytes Conficker.
Les étapes De Récupération Suppriment Malwarebytes Conficker.
Wiederherstellungsschritte Entfernen Malwarebytes Conficker.
Återställningssteg Tar Bort Malwarebytes Conficker.
As Etapas De Recuperação Removem O Malwarebytes Conficker.
Herstelstappen Verwijderen Malwarebytes Conficker.
복구 단계는 Malwarebytes Conficker를 제거합니다.
I Passaggi Per Il Ripristino Rimuovono Malwarebytes Conficker.